Safeguarding Innovation in the Fintech Sector- How and when to invest in cybersecurity
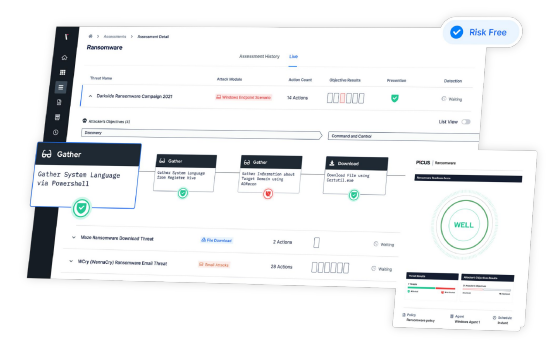
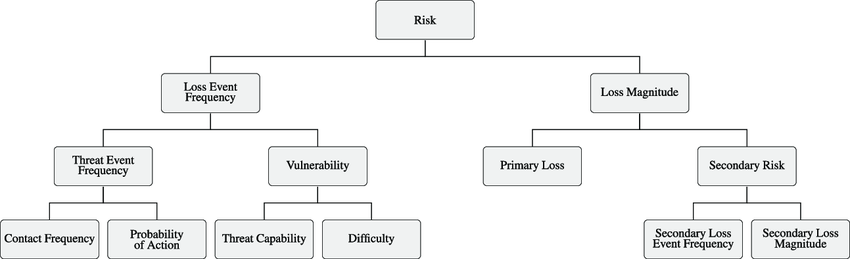
As Fintechs progress through their product lifecycle from Ideation to Expansive Growth, they encounter a myriad of challenges and opportunities, and there are always tradeoffs to be considered for allocation of resources; Cybersecurity is no exception. In this article, we will explore an approach to taking risk-based decisions around Cybersecurity investments and attempt to help …
Safeguarding Innovation in the Fintech Sector- How and when to invest in cybersecurity Read More »