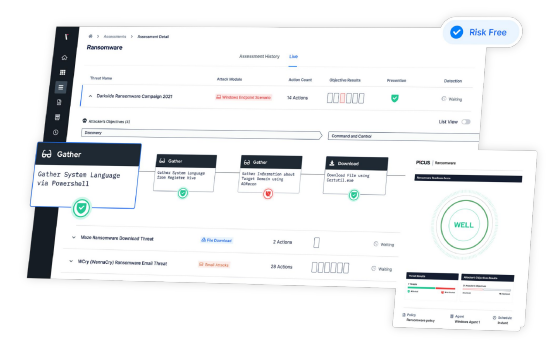
In today’s rapidly evolving digital landscape, enterprises across all verticals face a myriad of distinct cybersecurity challenges. For verticals such as Manufacturing, Healthcare and other Critical Industries that have significant technical debt coupled with limited funds/resourcing, it can be incredibly complex to safeguard assets from Ransomware and other cyber-attacks due to the constant change and traditionally time necessary to understand susceptibility to the latest attacks.
Techniques such as a managed Breach and Attack Simulation (BAS) service quickly provide clarity to the actual susceptibility of the environment to Ransomware and other cyber-attacks and allow the effectiveness of the control environment to be understood and quickly enhanced. Decisions can be made based on timely real-world testing, allowing organizations to set priorities and best use their limited resources to defend and protect key technology assets.
In this article, we explore how enterprises can harness the power of BAS to bolster their cybersecurity defenses, eliminate surprises, and take better, timelier decisions at a very compelling price point. By focusing on business imperatives and leveraging a managed BAS service, organizations can proactively identify their susceptibility to attacks, strengthen the right set of preventative and detective controls, and enhance overall cyber resiliency while not breaking the Information Security budget.
Understanding Managed BAS Services
Managed BAS services represent a proactive approach to cybersecurity that enables organizations to quickly assess and strengthen their security posture while also monitoring continuously for change. At its core, BAS involves simulating real-world Ransomware and other cyber-attack scenarios in a controlled environment to identify susceptibility to attacks and weaknesses. Here is a closer look at the key aspects of breach and attack simulation solutions:
Beyond Vulnerability Management: Continuous Visibility of Susceptibility
BAS replicates the tactics, techniques, and procedures (TTPs) used by cyber attackers to infiltrate networks, compromise systems, and exfiltrate data. These simulations encompass a wide range of attack scenarios, including malware infections, phishing attacks, Red Team exercises, Ransomware campaigns, and insider threats. By emulating these threats in a timely, safe and controlled manner, organizations gain valuable insights into their security posture, the actual susceptibility to specific Ransomware or other attack types, and gain clarity as to which controls provide the best bang for the buck or those that are not functioning as expected. Somewhat surprisingly, the INSIGHTS as to which controls are NOT functioning as anticipated often prove the most valuable. BAS managed services also provide specific, prioritized recommendations as to which controls need to be tuned and how this can be done with specific commands and examples. In essence, BAS serves as a strategic step up from traditional vulnerability management, providing organizations with far more specific and actionable recommendations to enhance their cybersecurity defenses.
Ongoing Assessment and Validation: Complementing Penetration Testing
Ongoing assessment and validation of susceptibility are core features of breach and attack simulation (BAS) services, particularly when managed by expert providers. Unlike traditional penetration testing, which provides a point-in-time assessment of security vulnerabilities, managed BAS services offer near-real-time and continuous assessment and validation capabilities. This allows for more frequent and timely evaluations of security controls and an accurate representation of the threat landscape. This approach not only enables organizations to identify emerging threats more promptly but also ensures that existent controls can remain effective and responsive to evolving cyber risks. By leveraging managed BAS services alongside penetration testing, organizations can realize a more comprehensive and proactive approach to cybersecurity assessments and risk management.
Resource Optimization: Automated Testing and Reporting
Managed breach and attack simulation (BAS) services offer a resource-efficient approach to cybersecurity assessment and risk management. Unlike traditional methods that require significant time and manpower, managed BAS automates the testing and results analysis processes, enabling organizations to conduct comprehensive security assessments with minimal internal resource investment. BAS solutions leverage advanced algorithms and attack simulation techniques to identify vulnerabilities, prioritize security risks, but it’s the expert knowledge that provides the most actionable INSIGHTS. Managed BAS services optimize the use of in-house resources, allowing organizations to focus their efforts on addressing the most critical security issues promptly rather than parsing several reports. This resource-efficient approach not only reduces the burden on internal teams but also ensures that cybersecurity efforts are cost-effective and aligned with organizational objectives.
Bolstering and Improving Existing Operations: Integration with SecOps
Breach and attack simulation (BAS) services seamlessly integrate with existing security operations workflows and tools, providing a significant enhancement to cybersecurity capabilities. These services are designed to work harmoniously with security information and event management (SIEM) systems, endpoint detection and response (EDR) solutions, and threat intelligence platforms all while evolving traditional vulnerability, patch, and threat management capabilities. This integration allows organizations to correlate simulated attack data with real-time security events, enriching their threat detection and the incident response capabilities of the SOC.
Elevate Your Cybersecurity with Managed Breach and Attack Simulation Services
Our managed BAS services offer a comprehensive approach to strengthening your organization’s cyber resilience. Through continuous security assessments, customized testing scenarios, and actionable INSIGHTS, we empower organizations to proactively identify vulnerabilities, enhance security controls, and mitigate the risk of cyber-attacks. With incident response support and ongoing security guidance, we ensure that your organization remains prepared to defend against evolving threats and maintain a robust and informed security posture. Contact us today to learn more about how our managed BAS services can elevate your cybersecurity program.